And Why Are We Talking About It?
We’re discussing Play-To-Earn ahead of Fanfest 2022, which starts on May 5. One part of the speculation about CCP’s upcoming announcements has been the discussion around cryptocurrencies, Non-Fungible Tokens (NFTs) and how emerging technologies can compliment EVE Online. One individual who has been at the forefront of recent discourse has been CCP Games CEO, Hilmar Pétursson.
“Gamers hope that the values created from online games can also be used in reality. The online gaming content should have practical values in the real world. The gaming industry should evolve to allow gamers to make retirement plans by using the money they earn from games.”
Hilmar Pétursson, CEO CCP Games
The Gist Of It
Put simply, modern Play-To-Earn (P2E) games use non-fungible tokens (NFTs) which represent in-game assets (such as items or in-game currency) to allow players to trade and sell those assets for real-world currency.
It Doesn’t Require NFTs
P2E games existed before the craze of blockchains took hold. My first experience with a similar system came with Blizzard’s Diablo 3 (D3). One of the major problems in Diablo 2 was real-world money trading (RMT) from third parties (RMTers). RMTers would sell items and gold to players for real-world currencies. To combat this, when D3 released it had an in-game auction house where you could sell items you owned for in-game gold or real-world currency. This system was designed to cut third-party sellers out of the loop by providing the same service from Blizzard itself.
This service was discontinued two months after the launch when the developers realized it made item acquisition too easy. This not only broke the game’s difficulty curve but removed the incentive to keep grinding for new gear (a core incentive found in many Blizzard games) by playing the game.
EVE Online and RMT
EVE Online also had an issue with RMTers selling ISK for real-world currency which it attempted to solve similarly by creating the Pilot’s Extension License or PLEX. PLEX could be bought from CCP games and traded in-game for ISK. It is a system that provides an authorized way to purchase ISK for real-world currencies from CCP.
However, unlike D3, in this case players in Eve Online were not able to trade ISK and receive real-world currencies. It has been a one-way system where players can spend real-world currency to acquire PLEX and sell PLEX for ISK. Players themselves cannot sell PLEX or ISK for real-world currency. This is commonly known as cashing out.
So, What Changed?
New P2E games use the advances in blockchain technology to provide users additional security for their in-game transactions for real-world currencies. This security system produces what’s called an NFT.
What is an NFT?
An NFT achieves its non-fungible status in this case using a cryptographic method called blockchain. Now, despite of all the recent uproar about blockchains, they are also in-fact nothing new. Blockchains were first imagined in 1982 by David Chaum. They have since become immensely popular with the advent of cryptocurrencies.
How Does Blockchain Work?
The driving layer of security for blockchains is the cryptographic hash. A cryptographic hash is a theoretical one-way function or algorithm. A one-way function is a mathematical function that theoretically does not have an inverse and cannot be decrypted, only reproduced. This means that it is very difficult, or impossible, to determine the inputs (such as a password) of the function based solely on its outputs (the hash).
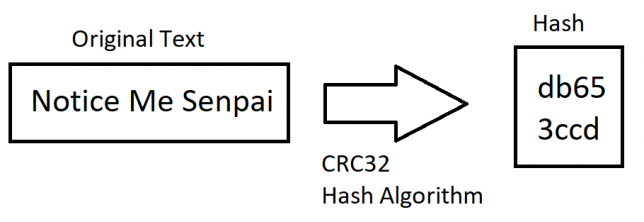
You can verify the image above by typing Notice Me Senpai (it is case sensitive and spaces matter) on this linked website by checking the CRC32 result. It will be the same as the image.
Since the only way to get the same output is with the same input, this allows the input to be verified. This allows hash functions to be used in digital signatures for non-repudiation (often called a key) and various other methods of authentication.
When your computer verifies your password, it simply hashes what you write and checks to see if it matches the hash stored in your system. Your passwords are technically not stored. The hash of your passwords is what is stored. Since a hash cannot be reversed (assuming it hasn’t been cracked) hackers have to guess your password, aka your key, to break into your computer.
Hash my Hashed Hashes Please
Block chains start with an often digitally signed (itself usually hashed) genesis block with the starting information. When verified and secure transactions occur, the data for the transaction is logged, hashed, and used to form a new block and a receipt is given to the buyer. When a new block is added (generally with each transaction) the location of the new data is given to the previous block. The previous block’s data is then copied, hashed, and stored in the current block. Since each block requires the hash of the previous block, this forms a secure immutable data chain that can be used to verify the logs.
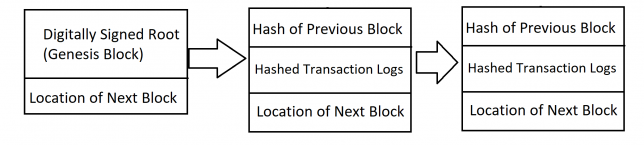
When done properly, this entire process creates an incredibly secure ledger of transactions. If you have a valid receipt, that receipt, and any other receipt, can be verified in the log by going through the chain.
It is further secured when used in a decentralized peer-to-peer setting such as Bitcoin where there is no single point of failure and the network can work together to fix errors and inconsistencies. Furthermore, the network can work together to authenticate new transactions. As a result, transaction forgery has so far proven to be exceedingly difficult. However, hackers tend to be quite imaginative in finding solutions to impossible problems.
One thing that humbles me deeply is to see that human genius has its limits while human stupidity does not.
Alexander Dumas, Great Universal Dictionary of the Nineteenth Century Vol. 2, circa 1865
The entire process is incredibly secure and verifiable. However, it assumes that the people with the keys are who they say they are. This is often referred to as the human element or the human factor in digital security. Despite such robust security, blockchain’s weakest point is people.
Honey, I Lost My Keys
One thing many companies that have online services will tell you is “never share your password with anyone.” If a hacker is able to determine your password with methods such as social engineering, it allows them to impersonate you to gain access the service, or services if you use the same password for everything. Now, if it’s just you, the only thing at risk might be say your bank account or crypto wallet. Which sucks for you but really doesn’t affect others. However, if—
You’re Special
That is something that can lead to some serious damage. An example of this is if The Mittani’s Jabber account were hacked, someone could order Goonswarm’s entire supercapital fleet into a PAPI woodchipper. Whether or not we follow the order is up to debate, but you get the picture.
Computers and their programs can also have keys, much like passwords, for authentication on networks. It gets even worse when a hacker acquires the keys to impersonate functions of a system.
Coming Full Circle
This happened recently in the nascent P2E scene when one of the largest P2E games called Axie Infinity was hacked and had 173,600 Ethereum ($625 million USD) stolen from the company. The hacker in this case acquired private keys of a system component and was able to impersonate several nodes of the network that validated the transfers from its in-house Ronin sidechain (a blockchain tied to another blockchain) to the Ethereum blockchain. After impersonating Axie Infinity and awarding themselves the power, they were able to make and validate transfers of Ethereum to themselves. This is not the first-time hackers have exploited a sidechain.
However, it should be noted that many sidechains take shortcuts when it comes to security. Shortcuts that cryptocurrencies such as Bitcoin and Ethereum do not take. Often sidechains take these risks because of a problem inherent to the blockchain’s secure structure.
It’s Really Slow
Blocks of transactions are verified and added to the blockchain in many cryptocurrencies through a distributed process to provide “proof of work”, “proof of stake”, etc., called mining. This “mining” occurs when a computer attempts to hash the transaction information for the block and offer to add its solution (as known as a block) to the blockchain. The blockchain network then chooses one block though a process called consensus and adds it to the blockchain. The miner whose block was chosen is often awarded some of the currency.
Blockchain and EVE Online
This process can take several seconds or several minutes to not only calculate the hashed solution, but also validate it and update the entire peer-to-peer network. This is not ideal for player markets such as Jita in Eve Online for items that move quickly.
While there may be room for NFTs in EVE Online such as rewards from CCP-run tournaments, individual player ships, player manufactured ships in the CCP store, or killmails, EVE Online was not originally built with NFTs or P2E in mind like Axie Infinity was. This means the people who play Axie Infinity know what they’re getting into. This is not the case for the EVE Online player-base should it turn towards P2E.
If P2E were made into a reality in EVE Online, this would cause resentment and boycotting, because the game the player-base spent years playing has changed into something completely different. I personally do not camp gates with my alt Khutef hoping to take away some of Pandemic Horde Member #22314’s retirement fund, as Hilmar put it. While I cannot speak for everyone, I could not PvP with such consequences. As made clear by this example, the very fundamental nature of EVE Online would change. Fundamentals that many would not agree to, and would thus opt to stop paying and playing the game. P2E still might come to EVE Online, but at least it will likely not include NFTs as a part of it.
CCP Says Not For Tranquility
CCP’s Hilmar recently posted an article titled “Blockchain and Eve Online” in which they claim “[CCP] have no plans to add blockchain technology into EVE Online’s global server Tranquility for the foreseeable future.” This is incredibly narrow in its scope. It only includes the main server Tranquility (TQ). This blanket of no NFTs does not include the EVE Online Intellectual Property, services or items related to the server, new NFT-based P2E EVE Online servers, EVE Echoes, new games CCP might be developing, or P2E schemes without NFTs. Since the profits from EVE Online seem to fund other CCP projects, it is somewhat worrying that it very precisely only applies to NFTs on TQ.
While this is reassuring for those opposed to NFTs on the main server, it also includes the prepositional phrase “for the foreseeable future.” This means that NFTs may be on the table should things change. It also means that CCP could change their mind at any time. We do not know how long the foreseeable future is. It could be days, weeks, months, or for the coming years as Hilmar put it. Because predictions of the future are not reliable, the promise of no NFTs in the foreseeable future is also not reliable.
Difficult to see. Always in motion is the future.
Yoda (Frank Oz), The Empire Strikes Back
The narrow and precise scope of the promise and the broad nature of its time frame does not inspire a lot of confidence. For now, it’s something as opposed to nothing. I am optimistic, at least for the foreseeable future, that NFTs won’t come to the TQ server.
While I have several years of experience working in information security and am currently studying computer science at my university, it is not my favorite subject. With all the technical aspects out of the way, we can discuss the more philosophical (my favorite subject) nature of the things NFTs represent.
What is Value?
The United States (US) Dollar once upon a time was backed by gold in a system known as the Gold Standard. This means that every dollar could be taken to Fort Knox in the US and exchanged for gold.
When the total value of the dollars in circulation started to far exceed total value of gold in Fort Knox, President Nixon directed the then Treasury Secretary Connally to suspend exchanging dollars for gold in 1971. After being decoupled from gold, the US Dollar became what is known as a fiat currency.
The value of a fiat currency is determined by the people who use it and not some external factor such as gold. It is, at its heart, a system of trust. People who trade material items or services for currency must trust the value of that currency otherwise they would not use that currency for trade. That trust is either earned or reinforced by its issuer. Which in this case is the US Government.
NFTs and Cryptocurrencies are like Fiat Currencies
It is true that both systems require trust when it comes to their exchange of their value. Due to the secure nature of blockchains, it is far more difficult to counterfeit a Bitcoin than it is to counterfeit a dollar. This gives many blockchains an edge over fiat currency when it comes to trust in the transaction. However–
Permanence
One of the primary factors in building trust is how long is the item being traded going to have value. This is often tied to the longevity of its issuer in the case of currency. While the US is a relatively young country at 233 years old (using the ratification of the US Constitution), the US is considered by many to have the most powerful military in the world. Combined with second largest nuclear arsenal in the world, it’s a safe bet the US Government is going to be around for a while.
Cryptocurrencies like Bitcoin will exist only if multiple people are willing and able to host the blockchain and authenticate transactions (adding more blocks) with their computers. Considering those who host and authenticate transactions have a self-interest to do it, it’s only a somewhat unsafe bet. If more people become accepting and trust cryptocurrency’s value, it has the potential to become a mainstream currency.
With that said, the opposite is true as well, and true most of the time so far. If less people accept and trust cryptocurrency, it will eventually collapse and become worthless. It will be known only as a fad or fraud (often called a rug pull). This is the fate of most new cryptocurrencies. Which, at long last, brings us to the similar system of game NFTs and game cryptocurrencies. To understand this further, we’re going to examine a popular P2E game called Axie Infinity.
Crypto-based P2E Games
Axie Infinity uses an inhouse sidechain called Ronin to handle their cryptocurrency called AXS. The developer makes money by charging a transaction tax when trading AXS for in-game NFTs or Ethereum. P2E games, like Axie Infinity, do not pay their miners like cryptocurrencies do. The company instead pockets the transaction cost in their sidechains that typically goes to miners in cryptocurrencies.
Should the game die (the fate of many games) and the company go under (the fate of many gaming companies), there is no incentive to keep verifying transactions and maintaining the blockchain. Therefore, games like Axie Infinity sidechain themselves to the cryptocurrencies like Ethereum as an exit strategy. When the players begin to cash out, the developer will also be cashing out.
Golden Parachutes
When a person quits Axie Infinity, they have the option to cash out their in-game assets to AXS and eventually Ethereum and real-world currencies. This means when the game faces a problem and begins to decline, Axie Infinity will make a lot of money from transaction taxes as users liquidate their in-game assets to Ethereum. This is the endgame. How they make money while the game runs is different.
How Do Players Make Money in Axie Infinity?
To start playing Axie Infinity, one must buy three of the pokemonesque Axies from the player marketplace. These Axie are made for new players, by veterans. As users play, they use the in-game currency called Sweet Love Potions (SLP) to breed and make new, more powerful Axies. Players either trade these new Axies to other players (using the AXS sidechain currency) or use them to obtain more SLPs in PvP. The higher the Match Making Rating (MMR) of the PvP battle, the more SLPs are awarded to the winner.
This means that players need a steady supply of less powerful, less skilled, often new, opponents to keep winning and making SLPs. This generally means the longer you have played in total, the more money you can make beating newer players. The entire system creates a hierarchy where the most experienced and powerful players at higher MMRs are selling powerful Axies to and making money off lower MMR players. Coupled with the initial investment of three Axies sold by veterans to new players, this is called—
A Pyramid Scheme
“a form of investment in which each paying participant recruits two further participants, with returns being given to early participants using money contributed by later ones.”
Google Dictionary
By removing the mysticism of the blockchain and understanding the monetization systems that drive the game, we can see Axie Infinity for what it is. While it might not be true of all NFTs or Cryptocurrencies, Axie Infinity is currently built as a pyramid scheme with a profitable exit strategy for the developers. P2E Games like Axie Infinity have been classified as scams by the Chinese Government, banned on Steam, and have been removed from stores in South Korea.
As we enter a new era in gaming where advances in blockchain technology allow for more secure transactions and verification of ownership, it is important to understand the basics of this system. As the length of this article touching the basics suggests, it is not a simple system. We must understand it to prevent ourselves from being caught up in scams (such as Axie Infinity) which look like successful ventures and judge what impact games (like EVE Online) transitioning to P2E with or without NFTs might have. Furthermore, we should ask if such robust and cumbersome security (designed for an open peer-to-peer network) is even necessary for the digital equivalent of a Monopoly® Property Card or Monopoly® money?

